A study on reduction of DDoS amplification attacks in the UDP-based CLDAP protocol | Semantic Scholar

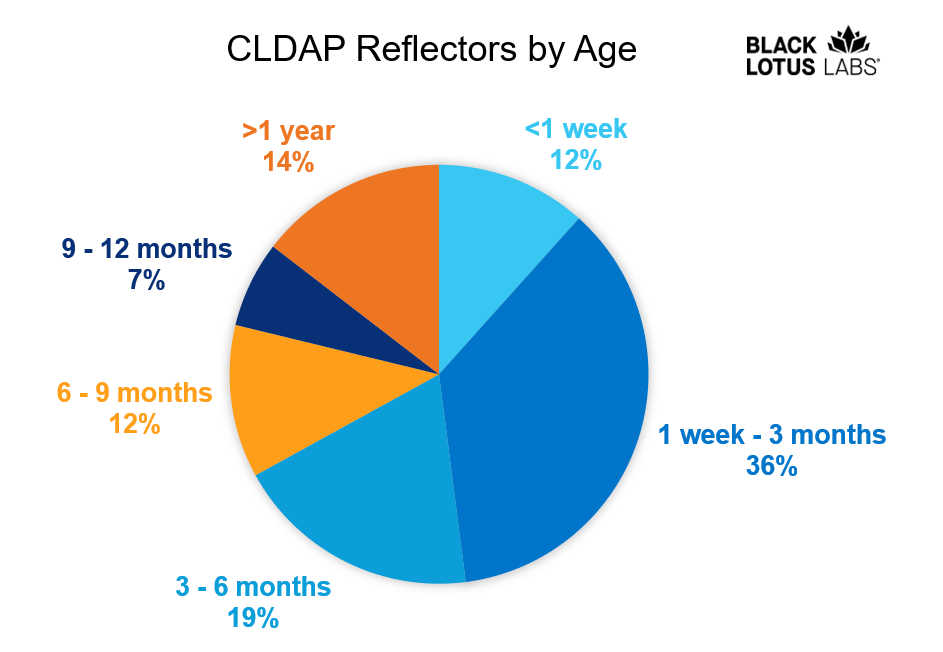
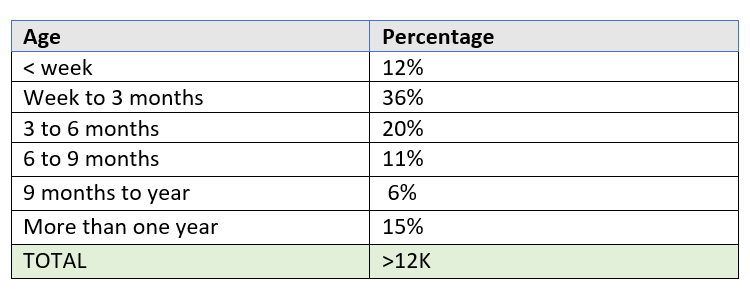
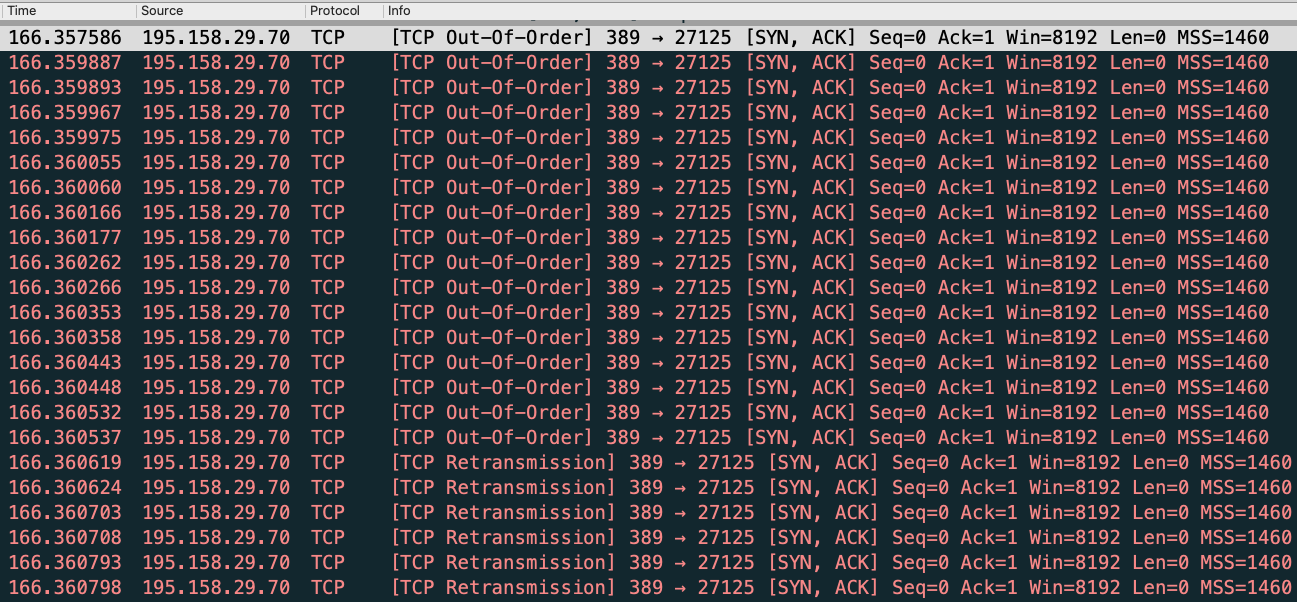
Black Lotus Labs al Twitter: "UDP amplification attacks are still a serious DDoS threat. The most commonly abused service today? CLDAP. We observed more than 281K unique IPs responding to CLDAP reflection

Blog elhacker.NET: Protocolo CLDAP permite realizar ataques DDoS con un factor de amplificación de 70x